Wep Key 128 Bit Generator Average ratng: 6,3/10 2766 reviews
Contents
Introduction
How do I set up 128-Bit WEP Wireless Security on a Cisco Small Business VoIP Router?
Related Information
Introduction
RandomKeygen is a free mobile-friendly tool that offers randomly generated keys and passwords you can use to secure any application, service or device. KEY RandomKeygen - The Secure Password & Keygen Generator. Aug 13, 2014 Download WEP key Generator - Simplistic piece of software that helps you generate valid WEP keys (64-, 128-, 152- and 256-bit keys) in order to secure your wireless connections.
This article is one in a series to assist in the setup, troubleshooting, and maintenance of Cisco Small Business products.
Q. How do I set up 128-Bit WEP Wireless Security on a Cisco Small Business VoIP Router?
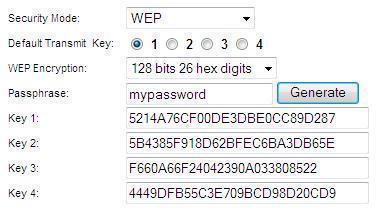
A.Wired Equivalent Privacy (WEP) is a 64-bit key with 10 hexadecimal digits or a 128-bit WEP key with 26 hexadecimal digits. This encryption will prevent other users from connecting to a wireless network using your own WEP key. It will also protect your wireless transmissions/communications from being accessed or received by other users.
In order to set up WEP Wireless Security on your Cisco Small Business router, complete these steps:
- WEP key strength (key length) is sometimes confusing because, although there are only two widely accepted standard lengths, 40-bit and 104-bit, those lengths are sometimes confused by adding the 24-bit IV (initialization vector) counter to the length, resulting in 64-bit and 128-bit total key lengths.
- WEP is the Wired Equivalent Privacy portion of IEEE 802.11b/g. Hexidecimal keys will be produced based on the de facto standard. Please note that Apple Computer uses.
- A 128-bit WEP key is usually entered as a string of 26 hexadecimal characters. 26 digits of 4 bits each gives 104 bits; adding the 24-bit IV produces the complete 128-bit WEP key (4 bits × 26 + 24 bits IV = 128 bits of WEP key). Most devices also allow the user to enter it as 13 ASCII characters (8 bits × 13 + 24 bits IV = 128 bits of WEP key).
Set up the VoIP Router to Use WEP
Wireless > Wireless Security.
Step 4:
Select any number under the Default Transmit Key in order to determine which key you will use. In this example, we selected number 1.
Step 6:
Type a wireless network password of your choice, such as 'MySecretKey' and click Generate.
Note: Create a password that is unique for your network and is a combination of numbers and letters up to 16 characters.
128 Bit Wep Key Generator
Wireless Encryption Security Information
|
Did this tool help you?
Please donate any amount through PayPal to help keep this handy tool online and FREE for all to use! |
| WEP Key Converter
Have you lost the password to your wireless router? Do you remember the simple codeword that you used the generate that complicated and impossible to remember code you need to connect? Use the form below to regenerate the key based on the pass phrase you used when setting up your router. Works with most Linksys, Netgear, Belkin, and DLink Routers. test Enter your ASCII pass phrase below and it will be converted into it's HEX equivalent.
| 64 bit keys:
1:
2:
3:
4:
| | 128 bit key: Hot Wi Fi Links! Wi-Fi is short for wireless fidelity -- used generically when referring of any type of 802.11 network, including 802.11b, 802.11a, and 802.11g. It is a trade term promulgated by the Wireless Ethernet Compatibility Alliance (WECA). 'Wi-Fi' is used in place of 802.11 in the same way that 'Ethernet' is used in place of IEEE 802.3. Products certified as Wi-Fi by WECA are interoperable with each other even if they are from different manufacturers. A user with a Wi-Fi product can use any brand of Access Point (AP) with any other brand of client hardware that is built to the Wi-Fi standard. Google definitions of Wi-Fi, Access Point (AP), hacker, freeware, SSID (Service Set Identifiers), MAC address, WLAN (Wireless Local Area Network), WEP, authentication, encryption, Denial of Service (DoS) attack. Wi-Fi Marketplace: HyperLink Technologies for a wide variety of useful Wi-Fi accessories. AirDefense.net recently published a White Paper which included the following Freeware software products available to hackers and white hat security researchers: NetStumbler for freeware wireless access point identifier - listens for SSIDs and sends beacons as probes searching for access points. Kismet for freeware wireless sniffer and monitor - passively monitors wireless traffic and sorts data to identify SSIDs, MAC addresses, channels and connection speeds. Wellenreiter for freeware WLAN discovery tool - uses brute force to identify low traffic access points; hides your real MAC address; integrates with GPS. THC-RUT for freeware WLAN discovery tool - uses brute force to identify low traffic access points. 'Your first knife on a foreign network.' Ethereal for freeware WLAN analyzer - interactively browse the capture data, viewing summary and detail information for all observed wireless traffic. AirSnort for freeware encryption breaker - passively monitoring transmissions, computing the encryption key when enough packets have been gathered. HostAP for conversion of a WLAN station to function as an access point. (Available for WLAN cards based on Intersil's Prism2/2.5/3 chip set) WEPWedgie for toolkit that determines 802.11 WEP keystreams and injects traffic with known keystreams in order to crack WEP in minutes. AirSnarf for soft AP setup utility that steals user names and passwords from public wireless hotspots by confusing users with DNS and HTTP redirects from a competing AP. SMAC for Windows © MAC Address modifying utility which allows users to change MAC address network interface cards (NICs) on Windows 2000, XP and 2003 Server systems, regardless of whether the NIC manufacturer allows this or not. You may also find interesting or useful: packetstormsecurity.org for an 'extremely large and current security tools resource.. maintained by a non-profit organization comprised of security professionals dedicated to providing the information necessary to secure the World's networks'. LXE White Papers on RF, RFID, Wireless and Bluetooth issues and Case Studies. Wi-Fi Alliance Protected Access (WPA) Security home page. What is YOUR IP Address - Click this link to find out! Mobile and Wireless Research being done at Xerox PARC.Endnote x8 2 product key generator. Copyright 2014 www.wepkey.com and www.webprecision.com email us! |
|
