Linux Openssl Generate Private Key
Lets say you have a private/public key pair that you use to login to your server via SSH and you lose the public key, either it was deleted or corrupt and you don’t want to have to regenerate a new pair what options do you have? In this post I will demonstrate how to regenerate a public key from the corresponding private key that you still have. Generate key pairs between geni nodes.
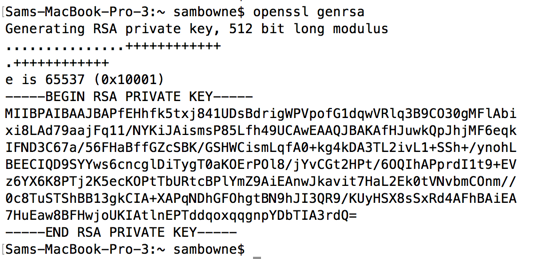
How to create a self-signed PEM file openssl req -newkey rsa:2048 -new -nodes -x509 -days 3650 -keyout key.pem -out cert.pem How to create a PEM file from existing certificate files that form a chain (optional) Remove the password from the Private Key by following the steps listed below: openssl rsa -in server.key -out nopassword.key Note. Office 2007 telephone activation key generator download. How to Decrypt an Enrypted SSL RSA Private Key (PEM / KEY). OpenSSL in Linux is the easiest way to decrypt an encrypted private key. Use the following command to decrypt an encrypted RSA key. Use the following command to create non-strict certificate and/or private key in PEM format: For public certificate (replace server.crt and server. Sep 12, 2014 Private Keys. This section covers OpenSSL commands that are specific to creating and verifying private keys. Create a Private Key. Use this command to create a password-protected, 2048-bit private key (domain.key): openssl genrsa -des3 -out domain.key 2048 Enter a password when prompted to complete the process. Verify a Private Key. Jul 09, 2019 Can I generate a new Private Key for my Certificate if I lose the old one? Normally, the CSR/RSA Private Key pairs on Linux-based operating systems are generated using the OpenSSL cryptographic engine, and saved as files with “.key” or “.pem” extensions on the server. OpenSSL has a variety of commands that can be used to operate on private key files, some of which are specific to RSA (e.g. Openssl rsa and openssl genrsa) or which have other limitations. Here we always use openssl pkey, openssl genpkey, and openssl pkcs8, regardless of the type of key. The first section describes how to generate private keys.
Generate public key and store into a file
It is a simple one liner command to generate a public key from a private key, so lets say our private key is named ‘user@myserver.key’ and we want to generate the public key and name it ‘authorized_keys’. Below is the command to do this.
‘> authorized_keys’: instead of printing the output to the console redirect the output (public key) to a file named ‘authorized_keys’
Copy public key to your server
Now we will need to take our authorized_keys file and store it on the server, if we can currently login via SSH to our server we can use rsync over ssh to securely copy the public key to the server, Although this key is displayed to anyone who attempts to login to your server it is smart to use SSH or another secure method to copy it up to the server to ensure that the key is not tampered with while it is being transmitted.
Below is an example using rsync to copy the authorized keys file to its destination on the server and removing it from your local computer.
Generate Key With Openssl
2 | user@server:~$chmod644/home/user/.ssh/authorized_keys |
Generate Rsa Key Openssl
At this point we are all set to begin using our private key to login to our server again. If you have any questions about this post please leave a comment below and if this helped you at all please share it on social media!